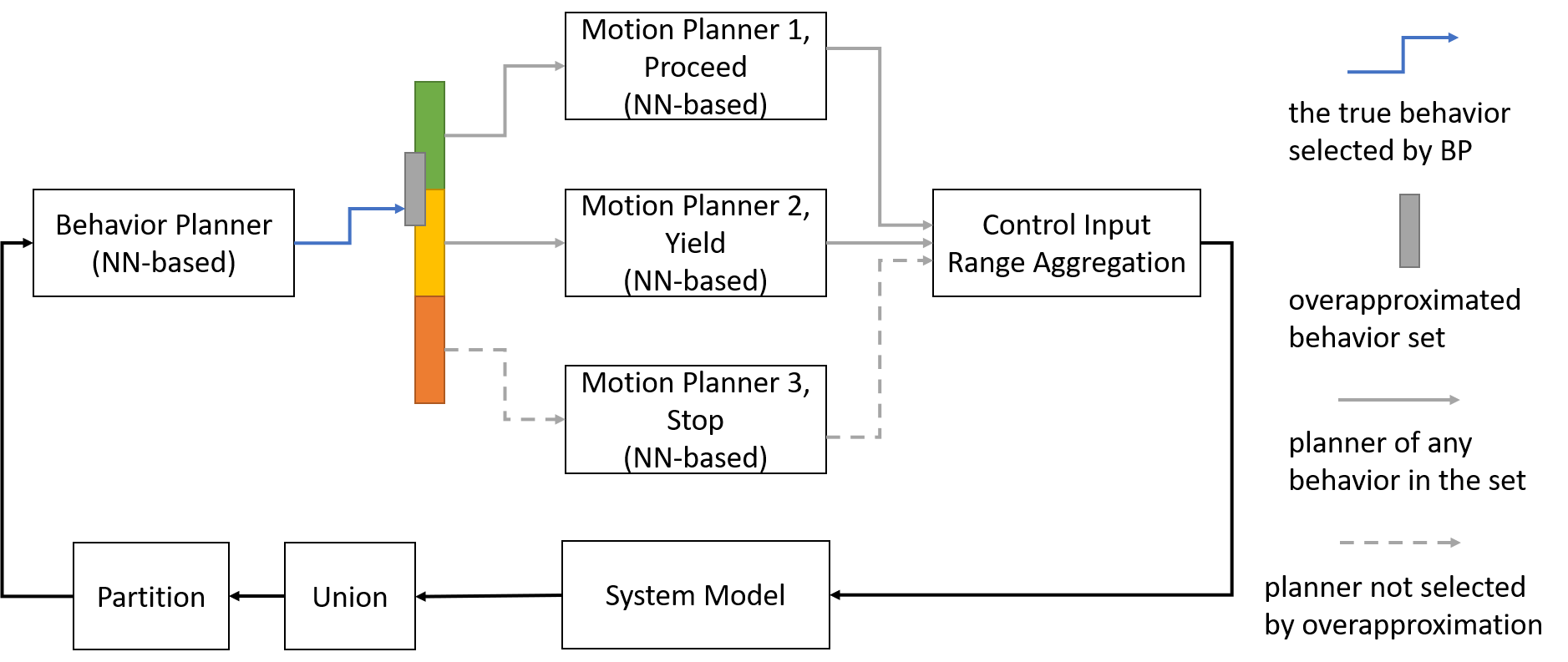
We have been developing design methodologies, adaptation strategies, and learning frameworks for controller synthesis and closed-loop control safety verification of safety-critical learning-enabled cyber-physical systems. Specifically, for the controller synthesis, we have developed methods for 1) energy-efficiently adaptation among multiple controllers with safety guarantees by control invariants, 2) learning a better neural network based controller from multiple existing controllers (either model-based or neural network-based) in terms of robustness, safety, and verifiability, and 3) learning a controller with reach-avoid property guarantees by holistically integrating the verifier in controller design. For closed-loop verification, we focus on perception neural network in the loop and have designed an efficient neural network global robustness certification framework to facilitate close-loop control safety verification.
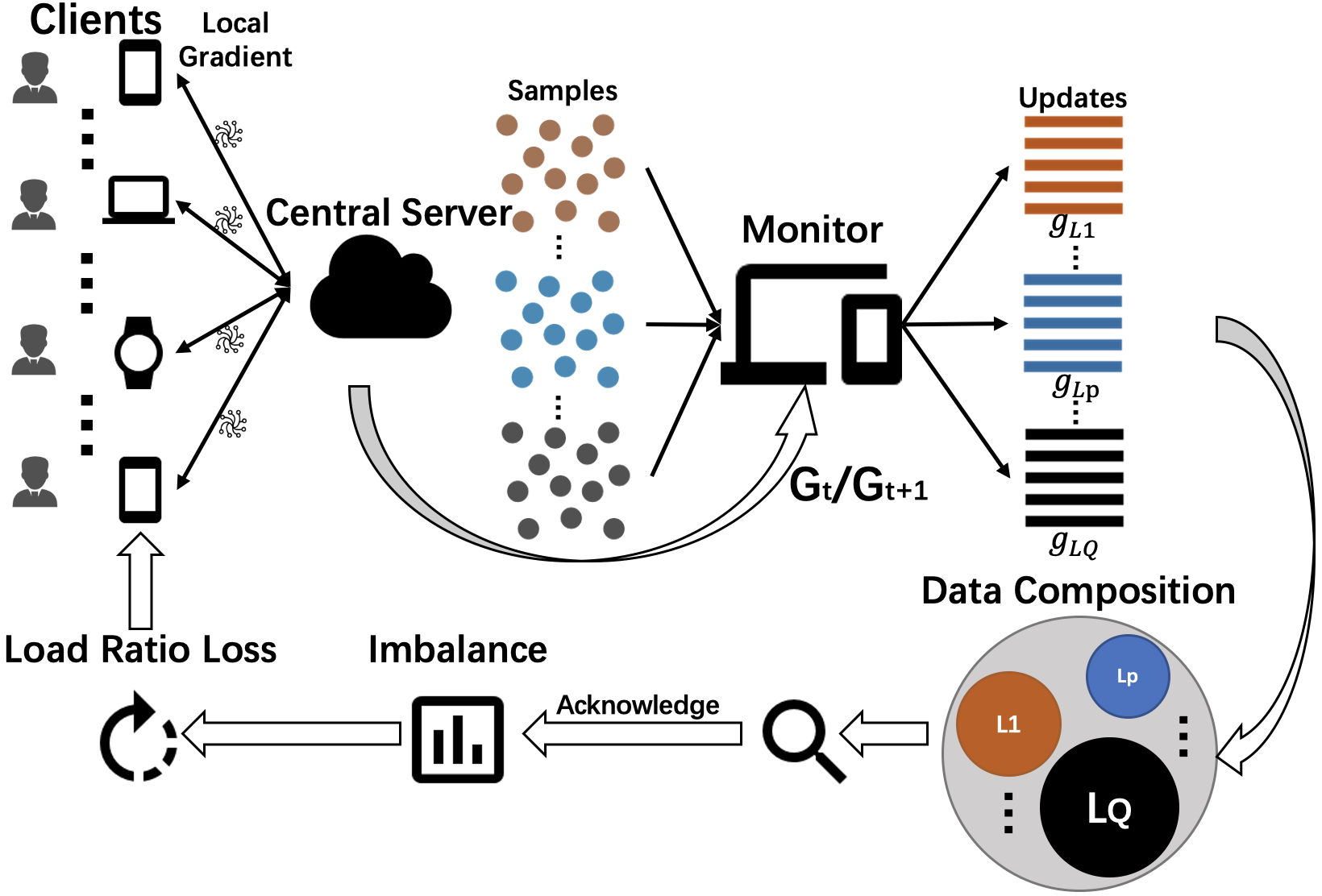
We address machine learning in practical cyber-physical systems with data constraints in Supervision, Generalization, and Privacy. In this direction, we have conducted a few research projects on Federated Learning (FL) and Transfer Learning. For the first FL project, we focus on mitigating the impact of class imbalance in FL, and we propose a monitoring scheme to detect the class imbalance and design a novel loss -- Ratio Loss to alleviate the impact. We then conducted a project related to the combination problem between FL and class incremental learning (CIL). For this project, we formally define the Federated Class Incremental Learning (FCIL) problem and propose a GLFC method to solve the problem. In addition, we are also interested in model protection and authorization across different data domains. For instance, contrary to the common goal of transfer learning, we propose a Non-Transferable Learning approach to protect the model intellectual property by model ownership verification and applicability authorization.
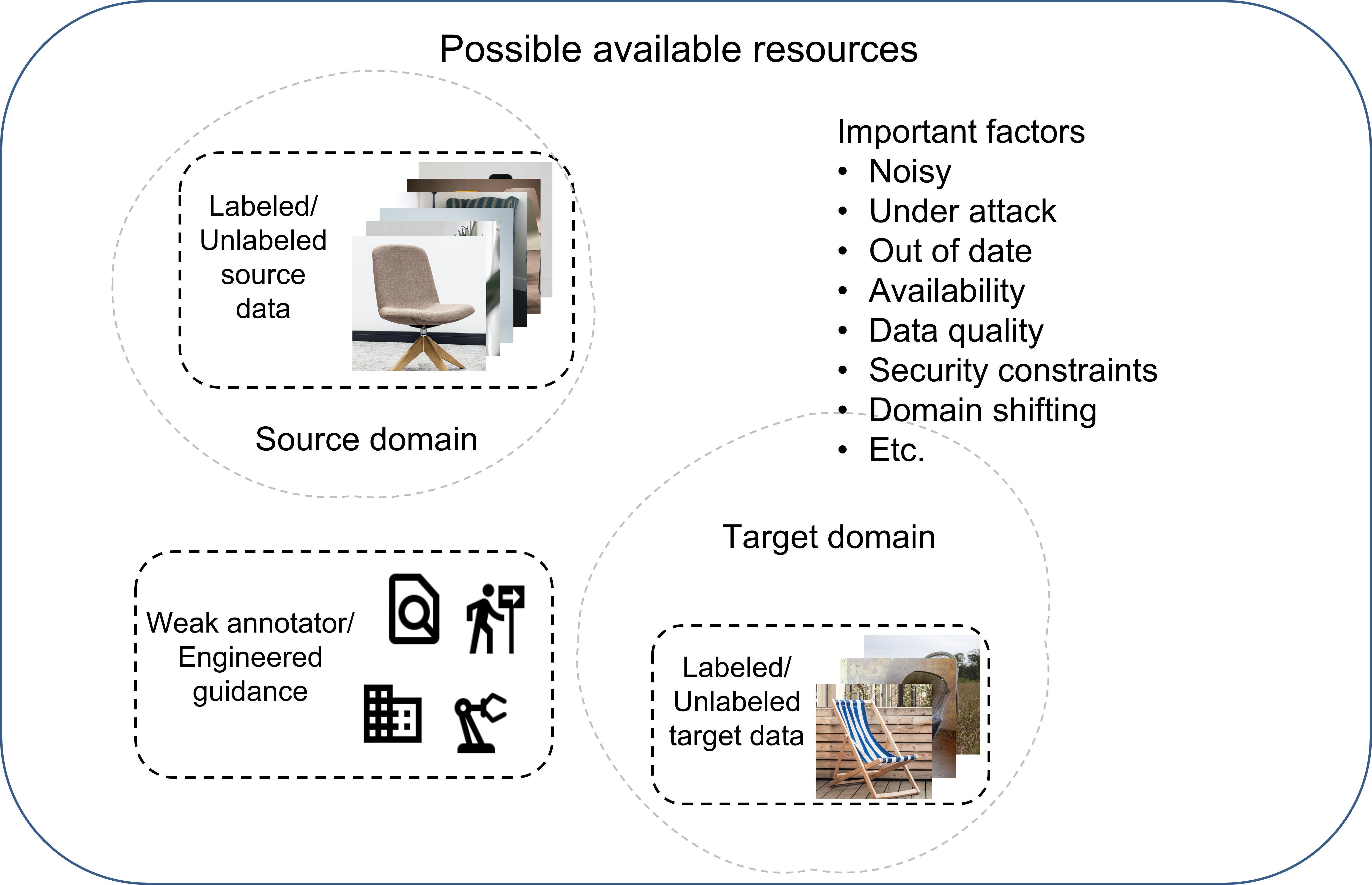
We are also addressing the machine learning challenges in cyber-physical systems that come from imperfect data, such as limited data availability, low data quality, disturbance and attacks to data, and challenges in generalization and adaptation.
We develop methods for conducting end-to-end analysis, design and verification of autonomous driving systems in order to make them perform better and safer in complex scenarios. In particular, we have developed uncertainty-aware end-to-end frameworks to mitigate the adversarial attacks against perception and localization modules. We are also working on designing efficient and reliable data-driven (deep learning-based) prediction modules to facilitate understating of the environment and safe planning.
We have developed methodologies and algorithms for the planner design, as well as addressing safety and security challenges in connected and autonomous vehicles. Currently, we are focusing on leveraging the underlying physical properties of the system, incorporating aggressiveness estimation and vehicular interaction in the planner design to improve system safety, verifiability, efficiency, and task success rate. We are also developing blockchain-based trust framework and temporal graph convolutional network-based scheme to defense attacks in connected vehicles.
We have developed methodologies, algorithms and tools for building real-world vision-based intelligent systems. In particular, We focus on on developing 1) adaptive visual algorithms that can automatically adapt to the changing physical environment, mission requirements, and resource constraints; 2) better perception algorithms for visual tasks; and 3) system-level design methodologies for building efficient vision-based intelligent systems, in domains such as mobile robots and next-generation connected and autonomous vehicles.
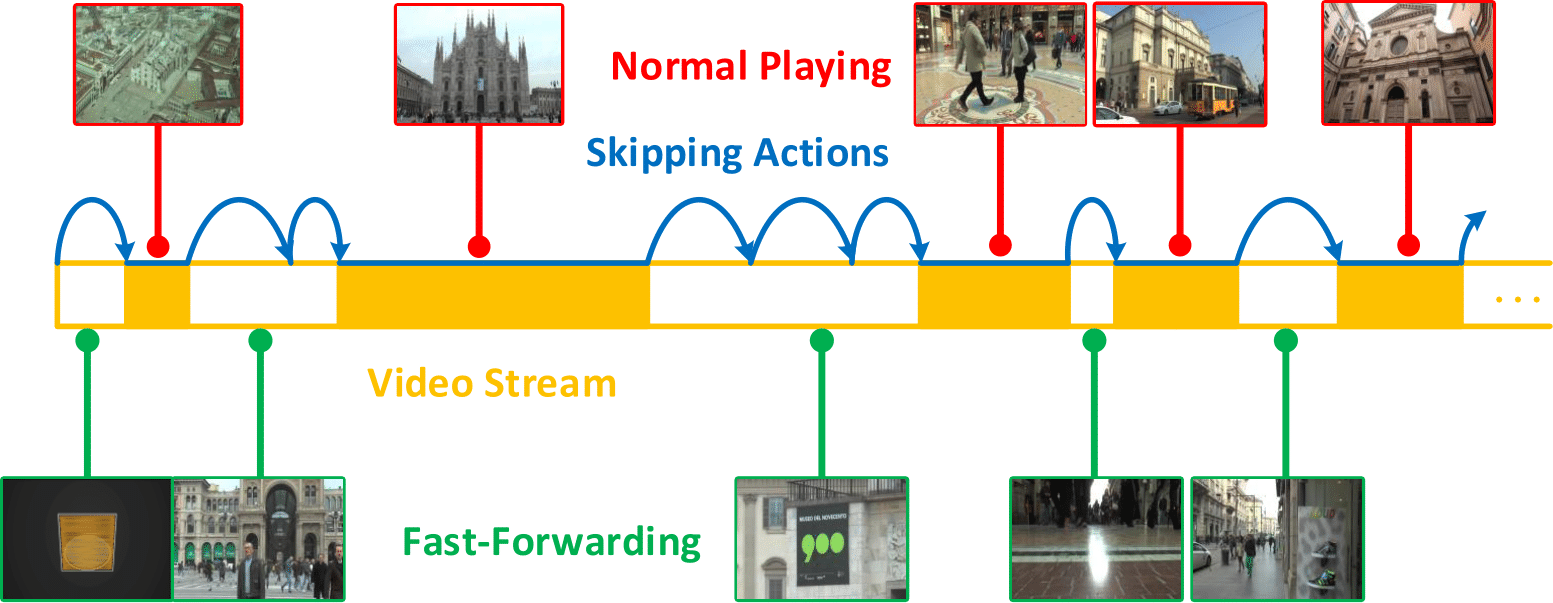
With growing system complexity and closer cyber-physical interaction, there are increasingly stronger dependencies between function and architecture layers in modern safety-critical systems. We focus on both the function and architecture layers, leverage the weakly-hard paradigm and propose cross-layer design and adaptation strategies for safety-critical systems. We present a cross-layer task period design method under the weakly-hard paradigm with the control stability guarantee. We also propose a runtime adaptation framework to improve system adaptability by allowing proactive skipping of task executions. For weakly-hard real-time systems, we introduce the metric of system extensibility and propose an efficient design algorithm that optimizes weakly-hard system extensibility.
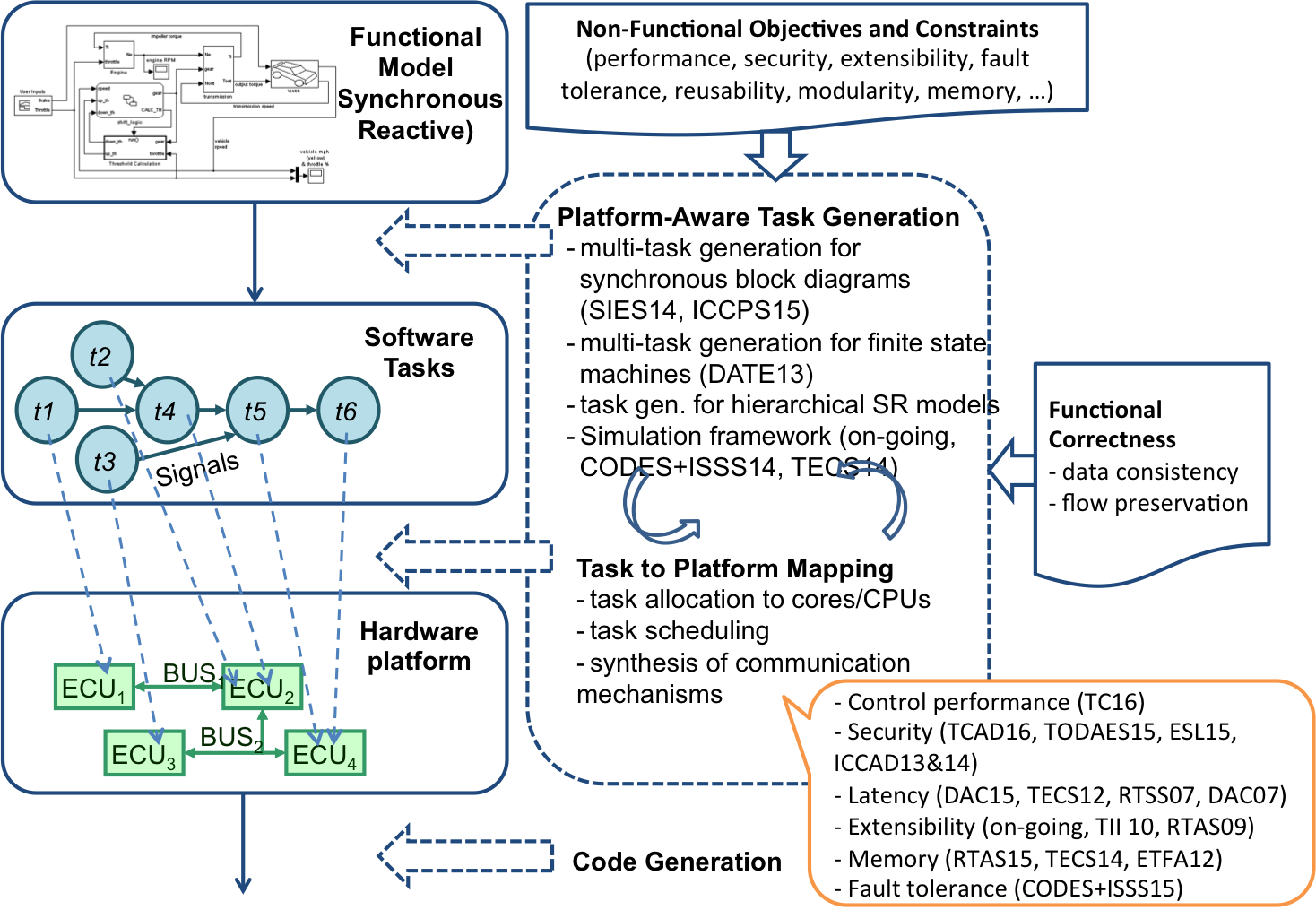
We developed a model-based software synthesis framework for cyber-physical systems. The framework optimizes the generation of software tasks from functional models and the mapping of those tasks onto embedded platforms, with respect to system safety, performance, security, extensibility, fault tolerance, reliability, memory usage, modularity and reusability. The framework is the first to address timing holistically throughout task generation and task mapping, and enables quantitative trade-offs with emerging design metrics such as security and extensibility.
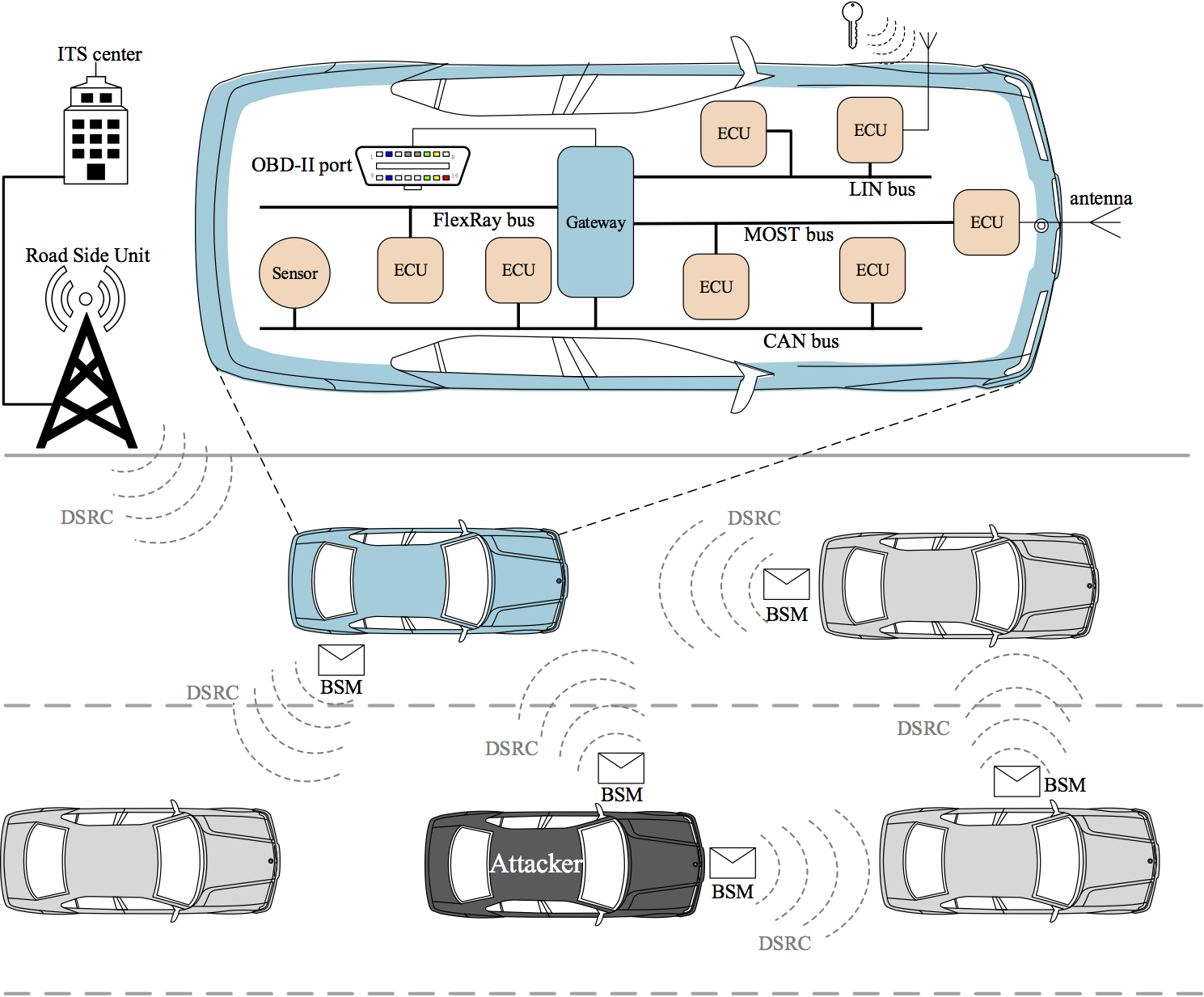
We developed a cross-layer framework for CPS security that integrates control-theoretic methods at functional layer with cyber-security techniques at embedded platform layer while addressing resource and timing constraints. It provides critical design capability to holistically cope with security and safety challenges in cyber-physical systems. We are exploring the application of this framework in vehicular networks. We have also developed algorithms for applying cyber-security techniques to the currently prevalent CAN (Controller Area Networks) architecture and to the next generation TDMA (time division multiple access) based automotive architecture, while considering resource and timing constraints.
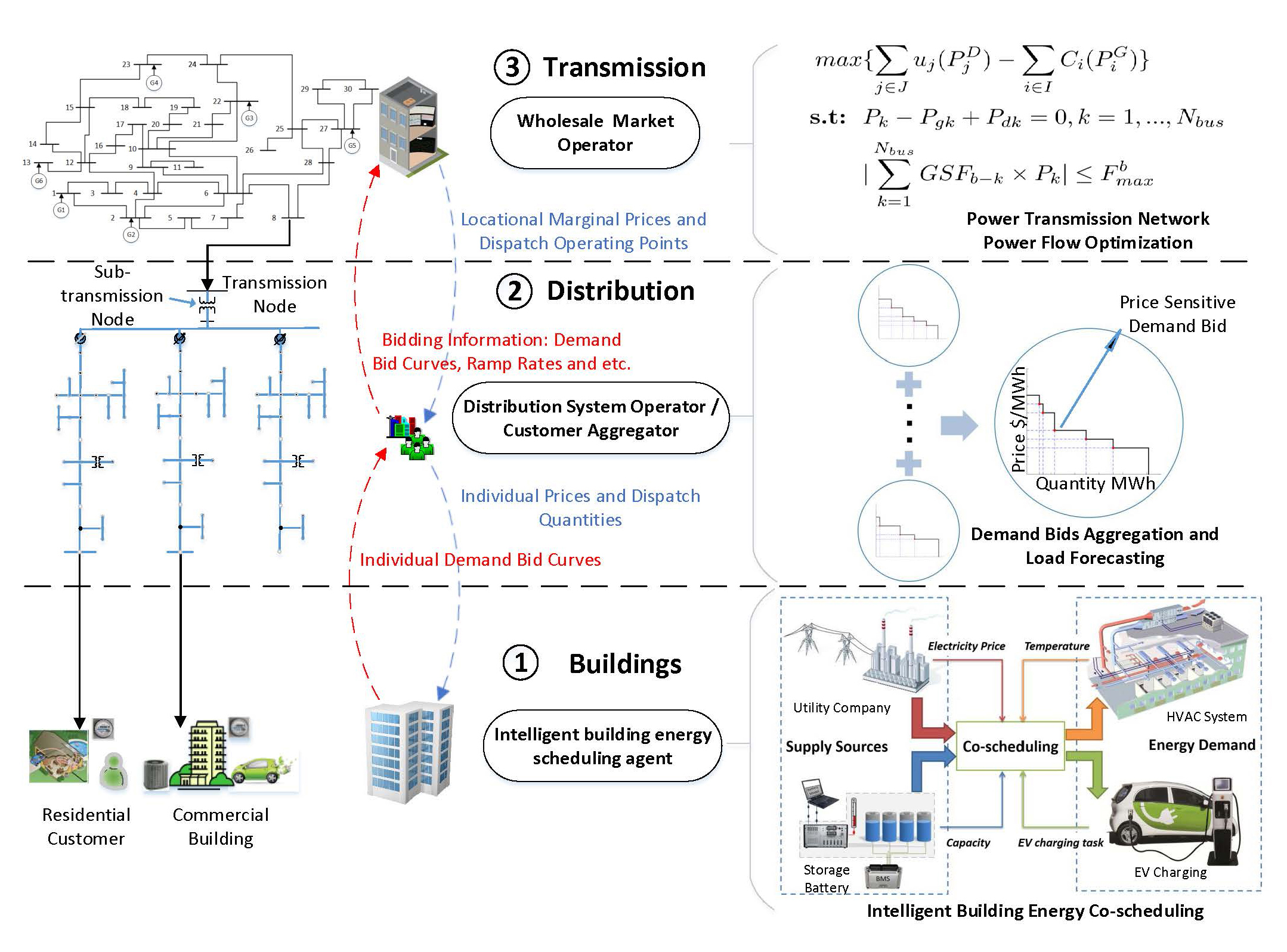
We developed methodologies and algorithms for improving the energy efficiency of buildings, including co-designing HVAC control and embedded platform, co-scheduling heterogeneous energy demands (HVAC, EV charging, datacenter operations) and supplies (grid, renewables, battery), and integrating intelligent building energy management with grid optimization through a proactive demand response framework.